ISO 27001 - Information Security Management System
ISO 27001 for Information Security Management Systems requires organisations to adopt a risk based approach to the security of all information. ISO 27001 is not a prescriptive document, rather it is intended to enable organisations to ensure the security of information through the assessment and treatment of information security risks, documented in a Statement of Applicability.
Information Security Management System Requirements
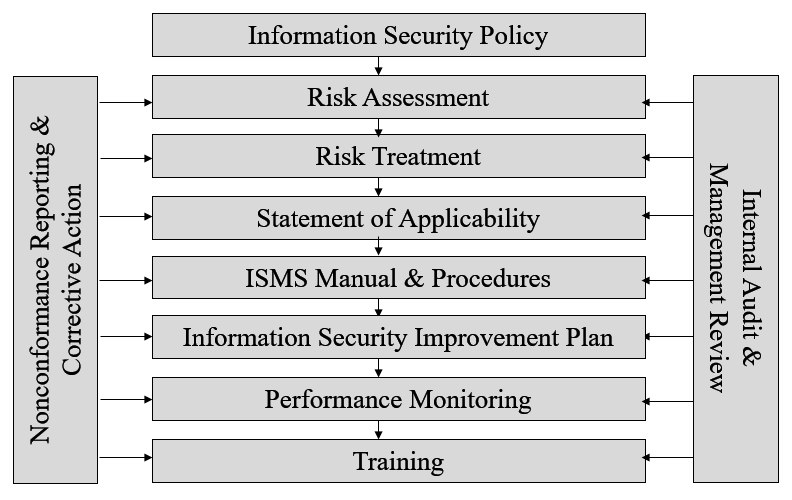
Information Security Management Systems (ISMS) require organisations to:
- identify information security risks
- understand external & internal issues, and interested parties, relevant to information security
- develop an Information Security Policy – typically one page document declaring commitment to information security
- develop a Statement of Applicability, documenting the assessment of identified information security risks and establishing controls (risk treatment) based on reference controls documented at Annex A of ISO 27001
- develop an ISMS or Management Manual – documenting as much or as little as you want but, typically, briefly addressing the clauses of ISO 27001; often integrated with the Manual for other management systems
- develop procedures –– instructions required to address information security
- control any outsourcing of information management
- develop and monitor information security objectives and targets
- embrace information security risks and opportunities throughout the business
- ensure staff are competent and understand their information security responsibilities
- monitor information security performance
- control information security nonconformances and take corrective action for significant or repetitive nonconformances
- conduct internal audits of the information security management system
- ensure senior management strategically review the information security management system.
Documentation Requirements
- Information Security Policy Statement of Applicability
- ISMS or Management Manual Procedures
- Improvement Plan (monitoring information security objectives and targets)
- Registers – nonconformances and corrective action.
Implementing an Information Security Management System
Benefits of an Information Security Management System
- demonstrated due diligence by meeting regulatory and customer requirements
- meeting international best practice for security
- meeting tender requirements and stand out from the competition
- improved reputation and enhanced company profile
- demonstrated integrity of data to customers, suppliers and other stakeholders
- reduced risk of fraud, information loss and disclosure
- increased resilience to cyber attacks
- prompt detection of data leakage and rapid reaction to breaches
- reduced costs associated with information security
- all forms of information, ensuring confidentiality, integrity and availability of data secured
- ensured workplace confidentiality and improved company culture
- easily integrated with other management systems.
TQCSI Certification Process
- contact your TQCSI Office and ask for a quote or apply on-line - TQCSI will need to know what your business does, how many employees (full time equivalent) and what types of information security risks are applicable
- to prevent delays, don’t wait until your Information Security Management System is fully implemented.
Certification Mark
Need Help?
Contact us here.